Governance and Control
Security-conscious enterprises with very tight control over how they manage and control the custody of their data.

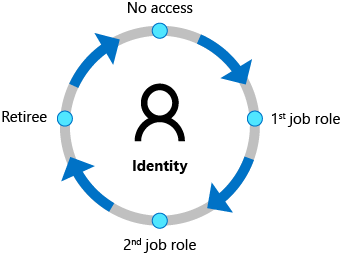
Identity Governance
As Azure promotes the least privilege model, there are variety of services like Identity Governance, Privileged Identity Management and Policies. Give access on-the-go to the new joiners and current joiners which make sure the data doesn’t leak in an event if something goes wrong.
Create Access Package
By creating an access package, you allow any one who requests that package full access to those particular resources for a time-bound access. Access Control examples: Sharepoint sites Groups Applications
Request Access
The user requests those resources and gets access to those resources after an approval process which requires proper justification as to why the access is required and for how long.
Approval
After the access is granted by the approver (if required), the user has full access to those resources to which he has granted access. For example, an accountant who recently joined requested access to the the account files.
Privileged Identity Management
As Azure promotes the least privilege model, there are variety of services like Identity Governance, Privileged Identity Management and Policies. Give access on-the-go to the new joiners and current joiners which make sure the data doesn’t leak in an event if something goes wrong.
Both Identity Governance and Privileged Identity Management helps us to give and revoke access and permissions but what PIM does is give permissions to the Azure Resources like VM, app service and several Azure AD roles such as global administrator, reader, etc. Have an internal review at the end of the month to see who had what access on what particular time. Sound secure, right ?
Azure Policies
With per-defined policies such as ISO 27001, HIPAA, PCI DSS, there is a lot you could do when you move to cloud. As an enterprise, you need to make sure that your data doesn’t leave your country and goes into wrong hands. You intend to make sure that there is a policy which blocks from creating resources at specific locations meaning they are barred from creating resources or make changes to certain settings to the resources. This is important when a lot of users handle IT and work hastily in order to get the job done.
Role-based Access Control
Role–based access control (RBAC) is a method of restricting network access based on the roles of individual users within an enterprise. RBAC lets employees have access rights only to the information they need to do their jobs and prevents them from accessing information that doesn’t pertain to them.
Grant them access to specific access like Virtual Machines, App Services, etc.


Azure AD Conditional Access
Conditional Access is the tool used by Azure Active Directory to bring signals together, to make decisions, and enforce organizational policies. Conditional Access is at the heart of the new identity driven control plane.
Block and Grant access based on the abnormalities of the user’s IP, location, device type, and times he has logged in and enforce strict policies like MFA which ensure protection.
Role-based Access Control
Multi-factor authentication is a process where a user is prompted during the sign-in process for an additional form of identification, such as to enter a code on their cellphone or to provide a fingerprint scan.
Azure Multi-Factor Authentication works by requiring two or more of the following authentication methods:
